Regex Crossword Solver with Z3
04 Jan 20161. Problem Statement
Regex Crossword (https://regexcrossword.com/) is a crossword puzzle where you fill in a rectangular board, so that regular expressions on every row and column are satisfied. It looks like this.
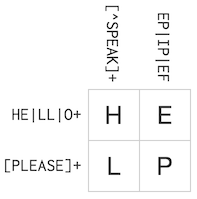
During fun geeky solving time, I thought it could be solved with computer. And actually there are great works with Regex Crossword solvers.
Herman Schaaf has solved it in Go-lang (http://herman.asia/solving-regex-crosswords-using-go). His solution analyzes the DFA generated by Go-lang’s regular expression compiler. His solution solves it really fast, that it only takes few miliseconds to solve one, but it cannot deal with backreferences.
Thomas Parslow has solved hexagonal version in Haskell (http://almostobsolete.net/regex-crossword/part1.html). His approach is basically same as solving by hand. He wrote a custom regular expression engine to do that. His solution can solve ones with backreferences, very quickly.
I’ve decided to take another approach, using SMT solver.